 |
| ECM Mark II, was known as SIGABA or Converter M-134 by the U.S Army, and CSP-888/889 by the U.S Navy. |
 |
| Note the rotors which are sitting atop the enclosure |
 |
| Rotor compartment |
 |
| Printer assembly |
| All photos in this table by Ralph Simpson |
The ECM Mark II , also known in the US Navy as CSP-888/889 or SIGABA by the Army, is a cipher machine. In one application , it was used aboard the USS Pampanito to encipher messages from plain text into a secret language called cipher text, under the control of a key (encipherment). A cryptographic system consists of the combination of cipher machine, operating procedures and management of keys. If the system is well designed and implemented correctly, cipher text can only be converted back to plain text (deciphered) by someone with all three elements of the system.In early September 1944, U.S.Fleet Radio Unit Pacific (FRUPAC) in Hawaii recorded a Japanese cipher radio message that originated from Singapore. Unknown to the Japanese, U.S. forces had analyzed many Japanese messages and as a result of much brilliant and hard work were able to reproduce their enemy's inadequately designed and implemented cryptographic system. This is called cryptanalysis or "breaking the system". FRUPAC deciphered (and decoded) the message that announced the route of an important Japanese convoy from Singapore to Japan. The timing and expected path of the convoy from the message was enciphered on an ECM in Hawaii and sent to Pampanito where it was deciphered on an ECM. Although Pampanito's crew did not know how FRUPAC got its information, they were able to go directly to the convoy's path and attack with great efficiency. Pampanito's attack was kept secret by the superior U.S. cryptographic system that revolved around the ECM Mark II.
 |
| ECM Mark II, was known as SIGABA or Converter M-134 by the U.S Army, and CSP-888/889 by the U.S Navy. |
 |
| Note the rotors which are sitting atop the enclosure |
 |
| Rotor compartment |
 |
| Printer assembly |
| All photos in this table by Ralph Simpson |
 |
| ECM Mark II (CSP 889/2900). This photo illustrates the blank paper tape placement Photo by Richard Myrick |
The ECM Mark II based cryptographic system is not known to have ever been broken by an enemy and was secure throughout WW II. The system was retired by the U.S. Navy in 1959 because it was too slow to meet the demands of modern naval communications. On top of that, the details of this machine were classified until April 1996. It was one of the top ten most important technologies of WW II,right up there with radar and proximity fuses but virtually nothing has been written about it because it remained classified for all those years.Axis powers (primarily Germany) did however periodically break the lower grade systems used by Allied forces. Early in the war (notably during the convoy battle of the Atlantic and the North Africa campaign) the breaking of Allied systems contributed to Axis success.
In contrast, the Allies were able to break Axis communications for most of the war supplying many of the targets attacked by Pampanito. Intercepted messages provided not only the location of potential targets, but often insight into the thinking of enemy commanders. In the Pacific, this information was critical to success in the battles of Midway and the Coral Sea in 1942. However, intelligence, including cryptanalysis, can be a double-edged sword. The intercepted message that directed Pampanito to attack the convoy during September 1944 did not indicate that 2000 Australian and British P.O.W.s were aboard the Japanese ships. The full story of this attack and Pampanito's rescue of 73 P.O.W.s is in the Third War Patrol Report. The combination of secure U.S. cryptographic systems and vulnerable Axis systems directly contributed the success of the Allied powers during WW II thereby shortening the war by years and saving countless human lives.
SIGABA was designed in the late 1930’s and discontinued in 1958. Approximately 11,000 units were built during WW-II [1].
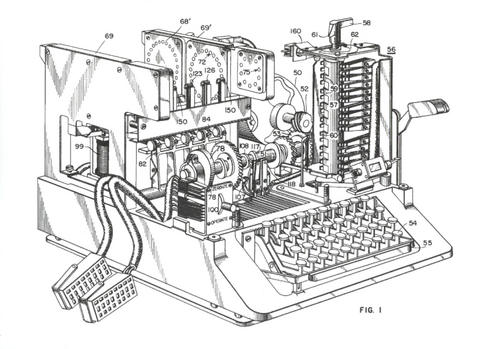 |
| SIGABA is described in U.S. Patent 6,175,625, filed in 1944 but not issued until 2001. The Cinch-Jones connectors attach to the Typing Unit which is not shown in this view. (Image courtesy Wikipedia) |
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
| Top |
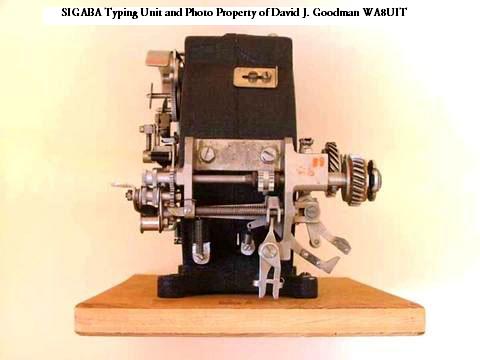
| Various views of the SIGABA the typing unit assembly made by Teletype
Corp. The assembly selected the characters to be printed,
struck the paper then advanced the ribbon and the paper.
It appears to have never been in service and was mounted on a shipping board when found. This is believed to be the only SIGABA major component in private hands. (Photos by David Goodman. Used with permission) |
| SIGABA typing unit - another view. (Photo by Nick England) |
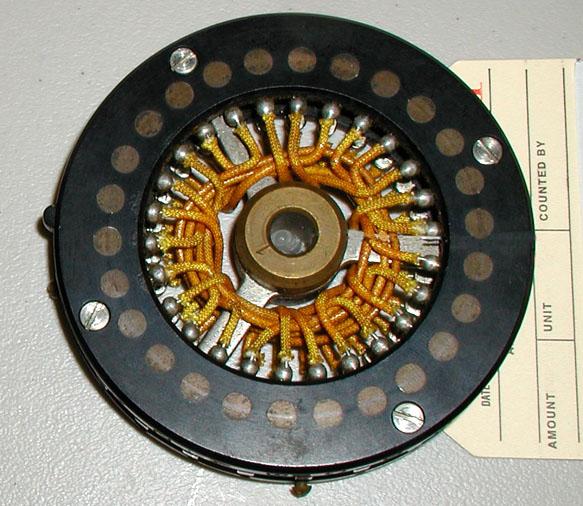 |
| Sigaba #1 rotor wheel. (Photo and copy courtesy David
Hamer, National Cryptologic Museum Foundation).
Wiring of SIGABA wheel marked M-134-C/CSP-889 and stamped ‘1’ : Index: A B C D E F G H I J K L M N O P Q R S T U
V W X Y Z
1. All wiring measurements made from left to right with the index
alphabet running vertically from A-Z.
|
Viewable here, is a story about the Colmar incident, where a SIGABA went missing and its surprising recovery.
FOOTNOTES:[1] United States Cryptologic History, Series VI the NSA Period 1952-Present, Volume 5, American Cryptology During the Cold War, 1945-1989, Book I; The Struggle For Centralization, 1945-1960, Thomas R. Johnson, Center for Cryptologic History, National Security Agency, 1995
Reference page 212 of the document.
Contributors and Credits:1) David J. Goodman <wa8uit(at)voyager.net>
2) http://en.wikipedia.org/wiki/Sigaba
3) Colmar Report http://www.nsa.gov/public_info/_files/cryptologic_spectrum/Colmar_Incident.pdf
4) David Hamer <dhhamer(at)comcast.net>
5) Ralph Simpson <ralphenator(at)gmail.com>
Sept 25/15