 |
| KL-7 photo courtesy John Alexander, G7GCK Leicester, UK). |
CODING OFFICE DESCRIPTION - 1962 FITTING
LOCATION : Part of Radio Room 1YEAR OF INSTALLATION : 1950.
CREW COMPLEMENT : As required.
PURPOSE OF THIS ROOM : To encode messages using a KL7 off-line encoding machine. There were two units in the Coding Office. Besides being a backup, the standby unit could be left with the previous days settings in case any late arriving messages had to be decoded. The crypto office was always locked unless someone was working in there. The KL-7 system was fitted around 1962.
TSEC/KL-7 Off-Line Coding UnitThis was an 8 rotor off-line cipher machine code name ADONIS, and was similar to, but more advanced than the famous German Enigma machine. It was used for the protection of exclusive (off-line) traffic. The unit had the approximate dimensions of a medium sized portable typewriter and was housed in an extruded aluminum carrying case which was painted in an olive drab, khaki colour. Navy versions, were of course, navy grey and the hinged case lid opened from front to rear. On the front of the KL7, there was a character counter to help keep track of the number of characters in a message and a small lamp to illuminate the keyboard. Rotor #4, not viewable, was maintained in a 'neutral' position.
Crypto-variables such as rotor settings were referenced from a hard bound paper code book or 'flash' paper bound into a small booklet. The KL7's used aboard HAIDA were powered from a 120 volt 60 Hz source. In the RCN, a complete second rotor assembly was stored in a separate box away from the machine. This assembly had the settings from the previous day and could easily be substituted in the KL7 to decode a late arriving message from the previous day.
 |
| KL-7 photo courtesy John Alexander, G7GCK Leicester, UK). |
To encrypt a plain text message, the operator would enter the message on the keyboard and the KL7 generated a gummed tape using 5 letter groups. The tape was pasted on a message pad and the resultant encoded message was submitted to the Message Centre where specific information such as Routing Indicators and Date-Time-Group was added. Finally, the complete message was passed to a radio operator or a Teletype operator for transmission. The system operated at a speed of 12 to 15 words per minute.To decrypt, coded messages were received in 5 letter groups. These, in turn, would be entered on the KL7 keyboard, and the machine would generate a gummed tape with the plain language text on it. This was pasted on a message pad and given to the message Centre where it was typed up and duplicated for distribution within the ship and for filing. According to Walt Hutchens, an ex-USN coder, "the noise produced by the KL7 rotors advancing was one of the two most distinctive sounds that I have ever heard. The other sound was the last round and the clip being ejected from an M-1 Garand".
Components for the KL7 and its variants were manufactured in the mid 50's to the mid 60's by several United States government contracted firms and the Singer Company was a major supplier. The parts were then assembled at either the Philadelphia Army Depot or at the Bluegrass, Kentucky plant. After final assembly, the units became the property of the National Security Agency and were distributed to the various military users. All crypto machines and materials were on loan to North Atlantic Treaty Organization member countries including Canada. In addition, there was also an airborne version of the KL7 which was modified at one of the US Air Force Security Service facilities in Mississippi for use in aircraft.
The KL7A was a battery powered version which had a higher degree of soundproofing to counter the problems produced by the acoustics of the machine. Batteries were not intended for portability, but for technical security reasons. Since the machine had a high TEMPEST and acoustical signature, there were concerns that it might be 'exploitable'. TEMPEST is an unclassified term that describes the vulnerability of an electronic device to having the classified components of its design intercepted and exploited. A machine that does not process classified information does not have a TEMPEST problem, only a radio frequency interference problem. Acoustical signature describes those systems which make an audible sound (sonic or subsonic or ultrasonic) which is repetitive and identifiable to certain specific functions. If these sounds are recorded from a distance, it is potentially feasible to compromise the machine.
After the Walker family spy ring was exposed in the mid 1980's, it was found that they had supplied the Soviet Union with a complete working KL7 and all keying materials. Immediately, all KL7's were withdrawn from service and returned to the COMSEC depot at Ft. Mead Maryland. This included all code books, spare parts, manuals and any other paraphernalia associated with the unit.
Another crypto system known by the code name of Orestes employed a device called the KW 7. Although not fitted on HAIDA, the KW 7 was an on-line, send/receive crypto unit installed in shore stations and aboard ships. It was used for ship to shore and for intership radioteletype communications. To send messages over a secure UHF teletype circuit, a model 28 Teletype or reader (T-D) sent the prepared message to the KW 7 which in turn keyed the TED3 UHF transmitter in the AM mode. Note, that the KW 7 was not a synchronous unit, therefore, it required a phasing signal to be sent in order to attain a lock on the received signal.
All of the crypto gear fitted on Canadian ships in the 1950's and 1960's was owned by the National Security Agency of the United States and was loaned to North Atlantic Treaty Organization member countries including Canada. Also included, was keying material, key lists, certain rotors, and key cards. This material came in a variety of editions depending upon the application. Examples of these crypto packages would be named CANUSEYESONLY, CANUKUS, AUSCANUKUS, NATO, ALLIED, and so on. Some of it was CANEYESONLY and would have been generated in Canada by the Communications Security Establishment.
It is interesting to note that by 1969 standards, the life cycle of a crypto system was generally set at 20 years even if the hardware didn't wear out. The KL7 and KW7 systems were still in use in 1969, long after their life expiry cycle. When crypto equipment was deemed surplus or obsolete, it was destroyed. Ships not equipped with on-line crypto equipment were considered to have a distinct time disadvantage in ship-shore-ship and inter-ship operations. The KL7 system was "life expired' as of 1969.
For a comprehensive look at the KL-7, select this link.
PREVIOUS CRYPTO OFFICE DEVICES
Bill Moffatt (LSCV1, RCN 1950-1955) recalls crypto operations in Korea. "During my service in HMCS Iroquois in Korea in 1952, one of my main duties was decoding messages. We used three systems.
1. One-time pad. - Messages were received in groups of five numbers. After selecting the correct starting place in the one-time pad (which was indicated by key groups), we subtracted the numbers on the pad from the
groups in the message and got the coded message, which we then decoded by using a code book.2. A British crypto machine called Typex. We inserted certain code wheels into the machine and set them at certain starting points according to key dates, etc. from a book. Typed in the encrypted message and the plain
language message was printed out on a tape.3. An American crypto machine called Adonis ( KL-7).
Our main difficulty with decoding messages was resolving messages that contained garbles. In doing this, we tried different combinations that could have resulted from incorrect reading of Morse code, that is, we substituted similar Morse code letters in the portion that came out as garbled, to see if we could determine what the original message had been and how it might have been corrupted by incorrect reception of the code. The other method of resolving garbled portions was the substitution of letters that could have been typo errors. Many of the messages were from agents in enemy territory and described the position of movements of NKA and ROC forces which had little to do with ships screening carriers or making island patrols on the west coast of Korea.
For my work on the Iroquois, I was given a Superior Efficiency Rating and enrolled in the Officer Candidate Program. However, I didn't follow up and left the navy after my term was up".
TYPEX
Andy Barber confirms that during the Korean war era, the Typex Mk 22 off-line crypto was fitted in the Crypto Office prior to the KL-7 . For additional details, select this link.
 |
| This is a post-war Typex Mk22 was lovingly restored to functional order and with two types of plugboards. The original plugboard jumper wiring was black, not yellow. This excellent recreation using modern wires illustrates the plugboard wiring. A good operator could do 40 wpm on the keyboard. (Bletchley Park photo via Wikipedia) |
PENELOPE - CSP 1750 (KA-2)
 |
| CSP 1750 (KA-2) (Photo courtesy John Alexander, G7GCK Leicester, England) |
The PENELOPE cryptosystem was designed to encrypt call signs and address groups used on radio circuits, both Morse and Voice. System components included keying materials and either of two associated devices designed for encrypting call signs and address groups in the form of four character groups, which were composed of any combination of letters and digits. For detailed information, select this link Dennis Stapleton conforms the use of the CSP1750 in the early 1950's and Al Goodwin says it was used into the 1960s.CCM (Combined Cypher Machine)
CCM was an “adapter” which permitted the same keying material to be used with the British Typex and American ECM Mk II machines. Typex and ECM were modified so that they were interoperable and supplied with common keying material . The major reason for CCM was that the Americans did not want to share ECM MkII machines with anyone else for fear that its secrets might be compromised. CCM was fitted aboard HAIDA in the Korean War era. A communuications problem study circa 1953 suggests that Tribals were fittex with both Typex and CCM machines
A photo of a CCM adaptation to a Typex machine is virtually impossible to find. For details on CCM, select this link
CCM Adaptation On Typex
The prerequisite for CCM adaptation is a Typex Mk 23. Specifically, a Mk 22 machine needs to be modified to a Mk 23 in order to accept the CCM adapter. The Mk 23 can be identified by the fact that it has an extra socket underneath the main one on the right hand side of the keyboard. It also has an extra lobe on one of the cams to trip the CCM. There are four long steel posts that are affixed to the base. The CCM adapter could not be installed in the field. It was a factory-only modification.
 |
| On this Typex Mk 23, the CCM adapter is not fitted along with the left and right plugboards. The CCM trip cam is not visible in this view. (Wikipedia photo) |
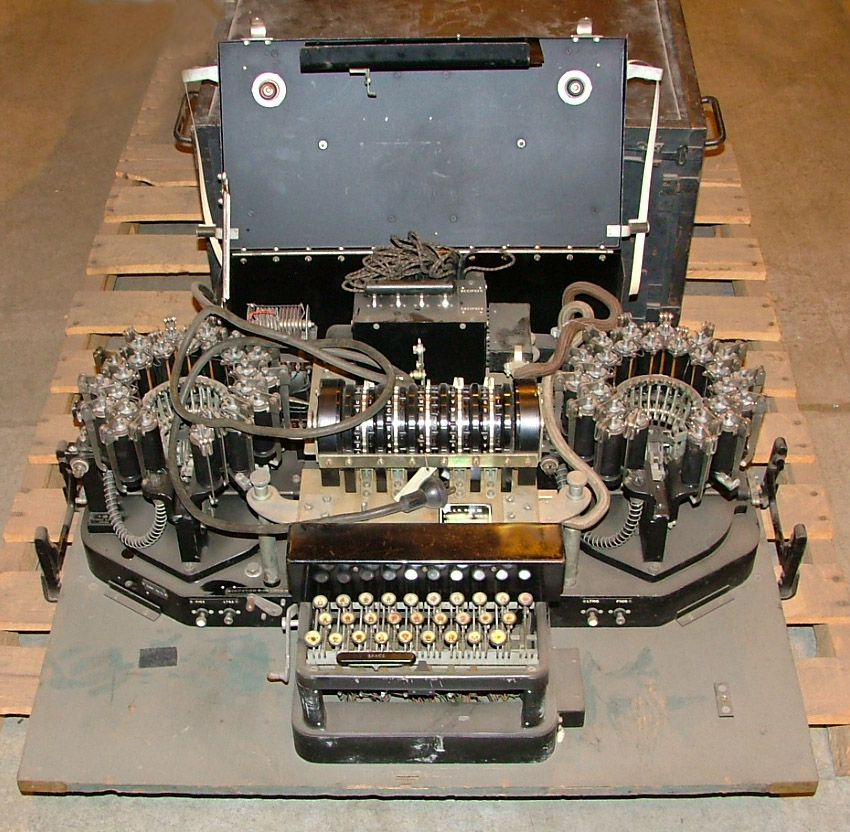 |
| Typex with CCM adapter installed and printing solenoid covers removed. Note that there are no plugboards in this machine. Not every Typex was fitted with left and right plugboards. Some had only one while others didn't have any. If plugboards were fitted, that would have given an extra degree of complexity to the machine when all that was required was compatibility with SIGABA. There were 186 different code systems used by Typex so even if the enemy had broken one, there would still be 185 others to try and break. One Typex maintainer recalls. "When I was servicing Typex in the RAF, the machines with the left and right plugboards were the worst to troubleshoot. Invariably the problems were caused by bad connections on the plugboard". (Photo courtesy National Cryptologic Museum via David Hamer, NCMF) |
Ron Mark served as a radio operator aboard HMCS Athabaskan in Korea. He remembers the following about crypto operations. "In Korea, we operated under the United Nations. CCM/Typex was a crypto machine used by the British and other Commonwealth Navies. CCM/SIGABA was a crypto machine in used by the American Navy.Some of the material we received on the broadcast was both Commonwealth and American crypto since the Task Force could be under American or British command. About 95 percent of the encrypted traffic on the ship was received on the broadcast. We used both the Type X and CCM machines to code and decode.
For ship-to-ship encoding/decoding, we used the appropriate machine, and if we were close enough to the ship it could be sent by CW or Voice on Inter-Ship circuits Otherwise it was sent to the broadcast centre for onward relay to the ship. During island operations and when working with Guerrilla groups, we used book code, stencil subtractor or the "Bicycle" machine.
The Bicycle machine was a set of small chains set into a box possibly 12 by 4 inches. It was non electric and portable. When set up, it would allow you to move the chain to get the desired output at the readout at the bottom of the box. It was mostly used in landing operations.
The Procedure For Receiving:
1. The message arrived at the crypto office usually typed by the receiving radio operator exactly as he had received it.
2. The crypto operator set up the date coordinates for the machine, then typed in the code, and the machine spit out the result and plain text on tape.
3. The crypto operator glued up the tape onto a message form and corrected any obvious spelling mistakes.
4. If it was routine message it was sent to the Message Centre to be typed up by a signalman. Then it was placed in the message log for viewing by the ships officers.
5. If the message was Operation Immediate or Flash, it was handed directly to the Captain or the Officer of the Watch on the bridge.
If the atmospheric conditions were bad or, if the radio operator was not on the ball, he could type some of the CW cypher groups incorrectly causing the encrypted message to garble. When the garble degraded the full meaning of the message, the Radio Office would ask for a resend of the message on the broadcast.
Messages about such things as the operation activity in the various off-shore Task Forces in Korea could run as high as 300 to 500 (FIVE) letter cypher groups. The traffic was transmitted at 25 words per minute or higher. One had to pay attention.
By the end of their Korean tour, experienced operators could layout the page to get an exact TEN of 5 letter cypher groups per line, but would then space them out by groups FIFTY. Then double or triple space by each ONE HUNDRED groups of code. If they were good, (as well as bored), they could divide each line in to five (5) letter cypher groups. Some of the printouts looked like a work of art. After six months of reading cypher groups, a good operator could do this while drinking coffee and smoking a cigarette.
When we went for R and R and supplies in Sasebo Japan, we shut down crypto operations in this harbour and kept a voice link with HMS Ladybird which was a British Commonwealth Headquarters Ship for the Far East Station. It was not a full time Naval ship and it look like a broken down river boat but it was on loan for the duration of the Korean War".
In HAIDA, locable stowage boxes were fitted into the Crypto Office during the refit of September 1959. This was a security improvement forthe storage of keying materials.
OTP (One Time Pad)In the RCN, the OTP was used to encode messages destined for smaller ships that could not justify the cost of crypto equipment. Al Goodwin (former POTEL) confirms the use of the OTP in HAIDA right from the Korean war era until the ship was paid off in October of 1963.
A one-time pad is essentially a pad of paper on which each page has a unique set of random letters. The sender and receiver have identical pads. Each letter on the pad is used to determine a single letter of the enciphered message. Since the letters on the pad are random, there is no formula that can be determined by studying the letters. Assuming that the pad is not compromised, and each page is used only once, then the OTP system is unbreakable. The disadvantage of the OTP system is that a copy of the pad must be securely delivered to the person on each end of the communication.
The OTP has not been been distributed to RCN ships for quite some time now. It is believed that the pad was abandoned sometime during the 1970's or even the 80s. For additional details on OTP, select this link.
Bill Janes of Perkins Quebec and Gregory McLean of Abbotsford B.C., focus on the problems associated with the disposal of classified material. "During World War II, there was no provision made on many ships for the filing of unclassified and classified messages. Sometimes the Telegraphists used their personal lockers for the storage of this material. Highly classified traffic was usually kept by the First Lieutenant or the Captain.As radioteletype was introduced into the fleet, it created an unforeseen problem - the voluminous disposal of classified waste. When the fleet broadcast used CW, only those messages destined for a ship were copied and decoded. This system left little waste paper and it could be disposed of easily. With the introduction of RATT, two or three ply paper was used to copy the broadcast. All messages would also be re-broadcast twice during a 24 hour period. With CW, messages had to be brief and code groups or common abbreviations were the rule. Non- essential items like book corrections and NDHQ promotions were sent my mail or courier to a Message Centre at the next port of call. You guessed it - every message was eventually sent over RATT including news summaries. This resulted in voluminous amounts of paper and disposal of this classified material became an immense problem.
When a ship became a guard ship for a squadron, it meant four ply paper was mounted in the Teletype machine and on certain occasions, six ply. With this many copies, the guard ship was now impacted with the paper disposal problem. The normal routine for the destruction of classified waste on Tribals was to burn it in the boiler. This was accomplished by taking the paper through the boiler room air lock and down a vertical ladder. Actual disposal was accomplished by opening a small inspection hole on the boiler face and feeding the waste paper into the boiler, a small quantity at a time. This activity was usually done each morning at the convenience of the Stokers rather than the Sparkers. This procedure was initiated by securing permission from the Engineer and Stoker on duty or alternately from the bridge. The burning of paper sometimes produced an intolerable amount of smoke from the funnel. On occasion, the Radioman would have to assist with a boiler cleaning when the Chief Engineer thought that the classified waste helped to foul the boiler tubing.
The method most often used in the 1950's and 1960's to dispose of classified waste was to burn it in a modified forty-five gallon oil drum. Radiomen would lash the drum to a rail on the upper deck near the funnel and the burning would commence. It is not known if this method was in common use on Tribals. One must appreciate that all of this paper had to be treated with the same level of consideration as filed messages - highly confidential. It had to be kept under lock and key and under guard if exposed. Much of the paper was burned in the ship itself but the RCN shore bases installed secure incinerators to help with the disposal of vast amounts of classified waste. The radio stations and dockyards on the east and west coasts had busy furnaces as did the Communication School at Cornwallis. Occasionally, incompletely burnt messages were found in the incinerators.
When the modern communication facilities at HMCS Aldergrove British Columbia were constructed in the mid 1970's, the destruction facility was located indoors and fuelled by natural gas. It was so efficient, that the RCMP used it to destroy marijuana and other evidence which was no longer required. On ship, the waste material was usually stored in the Classified Books Officer (CBO) storage area. When this became full, Radio 2 or Radio 3 was used as a storage area. Eventually, a shredder was fitted into the Message Centre to help alleviate the disposal problem. It would shred all waste to pieces measuring 3/8 inch long and 1/16 inch wide. When these shreddings required quick disposal, they could be mixed from garbage from the galley and thrown over the lee-side when outside territorial limits. Within territorial limits, the waste was stored within the ship and burned ashore.
There were also procedures in place for emergency destruction of coding equipment and classified material. Ships were equipped with weighted bags for the disposal of books and paper. Sledge hammers were to be used on equipment. If the emergency disposal procedure was invoked, orders were to destroy as much as possible. Machines were to be smashed with the hammers. Pages were to be torn from books and paper was to be hand shredded. If time permitted, the paper was to be thrown over the side. If the ship was in deep water, then the paper waste could be allowed to go down with the ship.
Ron Mark was a radio operator aboard HMCS Athabaskan in 1952. He adds the following. " On some ships, the paper waste was stored aboard until the ship sailed into a large port. You then took the ship's jeep and looked for a place that would have an incinerator i.e. Museum, Library, Naval Base etc or even a city park if you could find a cooking area. In Portugal we rode around on the jeep for 2 hours before we took the paper back to the ship to be burned at the next port. This was usually the job of the senior Leading Seaman or the Junior Petty Officer.
I cannot remember how the paper was handled in Korea, but I think it was stored until we arrived into the main USN base in Sasebo Japan. Then the paper was probably burned on one of the many USN support ships in the anchorage. There were no paper shredders in those days. Most junior radio operators would not be involved with the classified paper disposal as it would be a direct responsibility of the Chief Tel or Communications officer. There may have been other ways to dispose of classified waste that I am not aware of".
RECOVERING LOST ENCYPHERED CHARACTERS
Dennis Stapelton who served in the RCN in the early 1950s as a Radio Op, relates this story on how operators coaxed plain language from partially missed encyphered message traffic received in Morse code. "It was all dependent on the Morse operator being very specific and truthful on characters missed and where in the message the characters were missed. For instance, if the centre character in a 5 letter group was missed, the radio op would just type in a period. The decode op, when encountering the missing character, would just press the spacebar in lieu of the period. This would yield a faulty character, but the sequence and order is maintained and the original text could be be picked up on the next character and deciphering resumed.
However if the character stream was out of sequence, the entire remaining part of the message would be garbled. This recovery technique would also work if the operator copied a wrong character. As long as the sequence and order was maintained, only the missed character would be deciphered as a garble, however, the character missed would be only one letter in a word that could be easily deduced. This would be effective for any number of missed characters as long as the order was maintained and the radio op indicated where the characters were missed. If the garbled words or phrases missed could not be logically surmised because the importance of the message as a whole, a request for a resend would have to be made. The decode could still be viable if the radio op could correctly advise where the characters were missed, but the decode op would have to go back to the garbled character and, in a hit and miss manner, find where the decode could be picked up if possible. The word count on encyphered message of course helped in this regard".
ACCESS TO THE CRYPTO OFFICE
Normally a Signalman would decode an incoming coded message and then show the plain text decode first to the Captain. The Captain saw virtually every message addressed to the ship. He never had to enter the Crypto Office but it was certainly his prerogative to actually watch the message being decoded. The Captain never got involved with the mechanics of cryptography.
Contributors and Credits:
1) Ronald Mark <rondmark(at)shaw.ca>
2) Jim Guilford [jimguilford(at)gmail.com]
Sept 29/22